Information about your device has been stored for security purposes
We have identified that you do not have an account here, and your access has been granted at Level 1
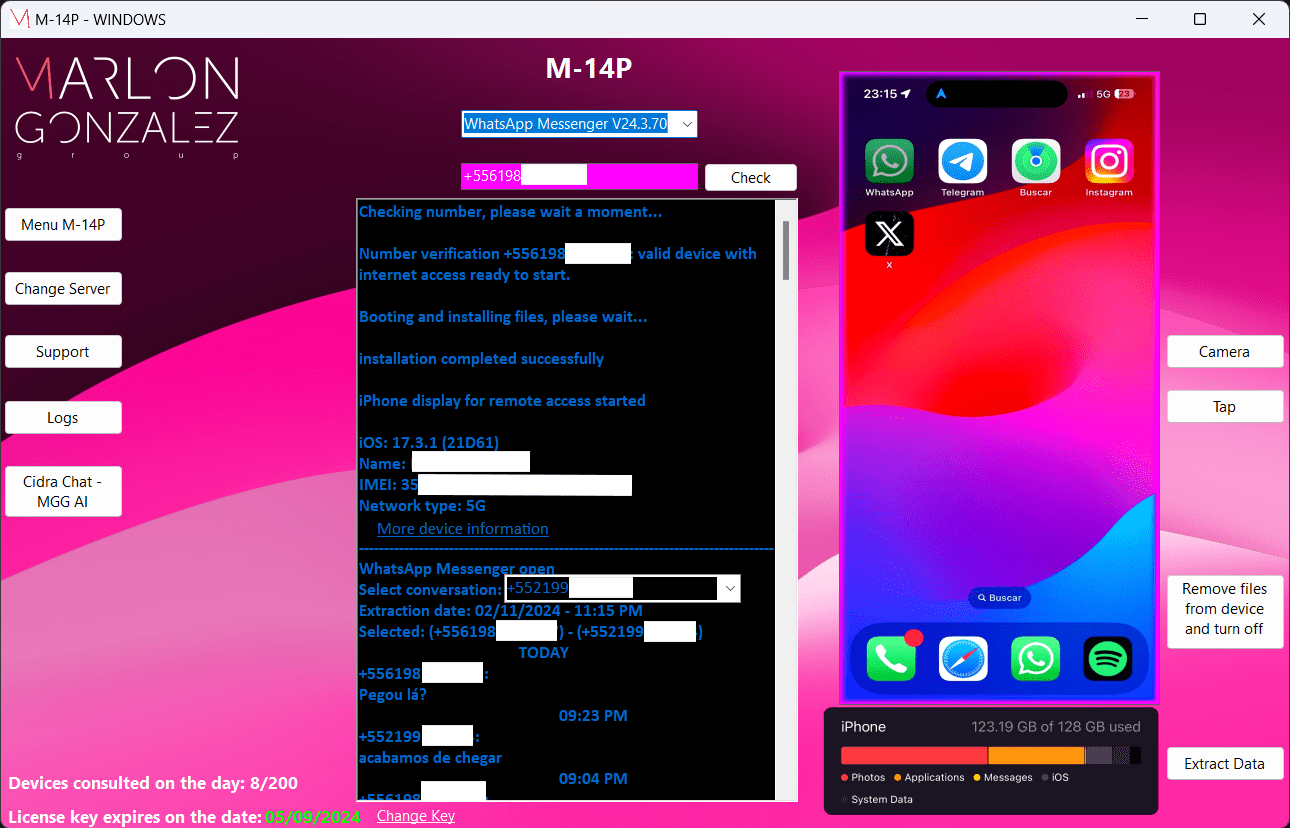
M-14P is a surveillance software for mobile devices exclusively for government intelligence agencies, capable of accessing iOS operating systems (18.2.1 OR LOWER VERSIONS) and Android (14 OR LOWER VERSIONS) without requiring physical contact with the device or interaction through clicks.
Activities within the device
If an application is in use and operating for the target user, you will be able to view its content, even if it is protected by Face ID or password. Check out some examples of common activities that you can access below:
WhatsApp is one of the most widely used messaging apps in the world. The M14-P can access all messages, viewing and extracting them from the device. It can also retrieve deleted messages.
Telegram
Like WhatsApp, Telegram is also one of the most widely used messaging apps in the world. The M14-P operates in the same way, with the option to view and extract everything to the local computer. Photos, videos, messages, audios, and anything else that is there.
Camera
The camera can be accessed normally, with the option to start recording at any time and send live footage to the software in local files. The video quality may vary greatly, depending on the type of camera and the stability of the connection. Therefore, video quality is influenced by a combination of factors.
Microphone
In the same way that it is possible to access and record the camera, it is also possible to do this with the microphone, with the listening option as an external option to start recording at any time. There is no time limit for the recording.
Cryptocurrency wallets
In addition to being able to access and view cryptocurrency wallets, such as Binance, Blockchain Wallet, or any other present, with a court order to block assets and funds, it is possible to move the defendant's cryptocurrencies to a justice-controlled wallet, causing them to disappear from the target's wallet. There are no limits to the transfer of cryptocurrencies.
Monitoring
Furthermore, it is possible to monitor everything that is done on the device while the target is using it, such as the websites they are accessing and what they are doing. It is possible to record these activities with a filter that starts recording whenever the device is unlocked.
Screenshot date: February 11, 2024, at 11:15 PM
Click here to view full-size image
Important
All intrusion products, including M-14P, are made available for a FREE 7-day trial. It is not possible to make any payment before obtaining the program and all its extensions and using them FREELY (with a limit of 200 target devices per day for each license) for 7 days to ensure the quality of our product. If, for ANY REASON, you do not like it, simply do not purchase it! That is our product guarantee: we assure you that you will be able to access any cell phone and manipulate it in any way, without restrictions. Please remember that we only sell to government intelligence services.
No red tape, with simplicity
No red tape to start using M-14P. Just contact us by email requesting a free trial with an email from the ".gov" domain of the government intelligence sector. No need to identify yourself or send any documentation, just the official domain of the intelligence sector is enough. We will send you a link for the 7 day trial download of M-14P, VPN, and the license keys for the 7 day trial.
Security Recommendations
Even though we are not responsible for how agents store information extracted from phones once it is on their computer, for security reasons, we recommend using a dedicated and isolated computer exclusively for M-14P, with no other software besides M-14P and our VPN.
Functionality Guarantee
| Version | Report Result | Date of the last test |
|---|---|---|
| iOS 18.2.1 | M-14P functionality tests successfully completed on iPhone 16 Pro Max and lower models. Functionality guarantee on iOS 18.2.1 (22C161) OR LOWER VERSIONS. | 2025-01-23 |
| iPadOS 18.2.1 | Successful functionality tests of M-14P on iPad Pro, iPad Air, iPad, iPad Mini with iPadOS 18.2.1 (22C161) and lower models. Guaranteed operation on iPadOS 18.2.1 OR LOWER VERSIONS. | 2025-01-23 |
| Android 14 | M-14P functionality tests successfully completed on various brands. Functionality guarantee on Android 14 OR LOWER VERSIONS. | 2024-02-24 |
Legal Considerations
Apple Inc:
Not Affiliated with Apple Inc. M-14P is provided independently and has no affiliation with Apple Inc. or its affiliates, directly or indirectly. Apple, AAPL, iPhone, iPad, iOS, MacOS, Mac, Apple Vision, Apple Watch, watchOS, Apple TV, AirTag, and other related product names and logos are trademarks of Apple Inc. Apple is not responsible for M-14P, its content, or functionality.
Pegasus Spyware - NSO GROUP:
Not Affiliated with NSO GROUP. M-14P is independently developed by the Marlon Gonzalez Group and has no affiliation with NSO GROUP or Pegasus Spyware, or their affiliates, directly or indirectly. The list of indicators included by AmnestyTech and Citizen Lab, such as domains.txt, v2_domains.txt, v3_domains.txt, v4_domains.txt, v4_validation_domains.txt, emails.txt, files.txt, pegasus.stix2, and processes.txt, has no connection to M-14P.
M-14P Usage:
The M-14P software and the Marlon Gonzalez Group do not support, tolerate, or endorse the use of their software for illegal activities. This includes, but is not limited to, the theft of cryptocurrencies from unauthorized devices, non-national security-related espionage, non-security-related use, or any action targeting human rights activists, journalists, politicians, and other individuals, provided that such actions are not linked to crimes or national security.
Other M-14P Issues:
• Even though extractions and connections pass through our servers, we do not store any information from the targets. The responsibility for storing what has been extracted, as well as making backups of the extraction, lies with the intelligence agent responsible for the operation. After the data transit is successfully carried out and stored on the agent's computer, the Marlon Gonzalez Group is not responsible for how the agent stores the content on their computer or for improper storage practices, such as lack of information backups.
• The Marlon Gonzalez Group shall not be responsible for the decisions made by intelligence agents regarding the targets. We are only software developers and do not control, limit, or have knowledge of what is being done. In case of violation of usage guidelines, we may suspend the next annual license renewal.
• We work tirelessly to maintain the highest level of anonymity and always strive to improve extraction as discreetly and equitably as possible. However, we are not responsible if a device breach is detected during an investigation. We are not responsible for the traces left behind.
• No one in the Marlon Gonzalez Group uses the tool for personal use under any circumstances, which would be considered a crime. We always seek legal means to resolve issues.
1-Year License Budget (Consultation and limited extraction to 200 devices per day per license)
US$
5.319.000,00
Download M-14P
Transparency
Details about the information we store about you to ensure your safety
Your IP:
Your Country:
Your State:
Your City:
Your Internet Provider:
Your Operating System:
Your User Level: 1
Your Date and Time:
Records of your access have been temporarily stored securely, protected, and encrypted in the Marlon Gonzalez Group's database successfully.
MGGHASH: